#PowerShell Core
Explore tagged Tumblr posts
Text
Recall is only on specific PCs. When you purchase a PC with Recall it should specify on the box that it's a PC with Copilot+ and Recall, I believe it uses snapdragon.
Normal users with their six+ year old PCs that have regular and cheap processors with windows 11 or 10 will have Copilot which is the AI thing that can be disabled via powershell or just turned removed from the taskbar in settings.
Even users who buy new PCs now are not going to get the ones with Copilot+ and Recall because they are not typically being marketed to normal users who don't use Windows features, but are being marketed to business users instead.
I understand that this is a horrible thing and I do not agree with it, but your normal core i5 PC with an Intel card that you play steam games on and watch youtube videos on is not the target of this.
Literal definition of spyware:
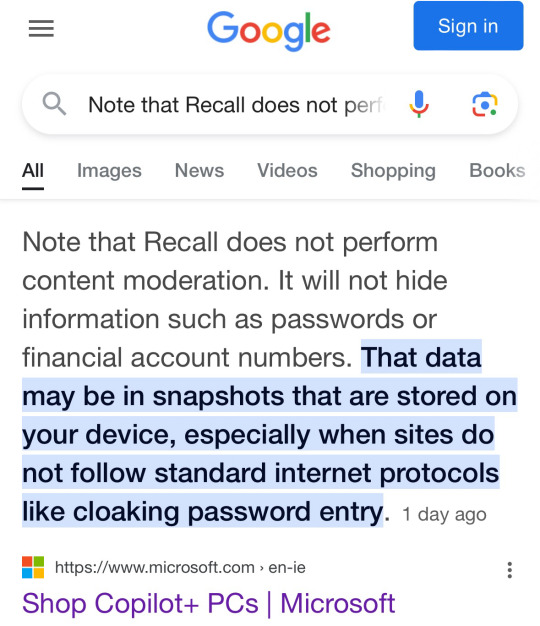
Also From Microsoft’s own FAQ: "Note that Recall does not perform content moderation. It will not hide information such as passwords or financial account numbers. 🤡
#sorry i dont mean to add onto this#but even at my job we have yet to come across any of these PCs at any of our clients
248K notes
·
View notes
Text
Metadata Management After Moving from Tableau to Power BI
Migrating from Tableau to Power BI is a strategic decision for organizations looking to centralize analytics, streamline licensing, and harness Microsoft's broader ecosystem. However, while dashboard and visual migration often take center stage, one crucial component often overlooked is metadata management. Poor metadata handling can lead to inconsistent reporting, broken lineage, and compliance issues. This blog explores how businesses can realign their metadata strategies post-migration to ensure smooth and reliable reporting in Power BI.
Understanding Metadata in BI Tools
Metadata is essentially "data about data." It includes information about datasets, such as source systems, field types, data definitions, relationships, and transformation logic. In Tableau, metadata is often embedded in workbooks or managed externally via Data Catalog integrations. In contrast, Power BI integrates metadata tightly within Power BI Desktop, Power BI Service, and the Power BI Data Model using features like the Data Model schema, lineage views, and dataflows.
Key Metadata Challenges During Migration
When migrating from Tableau to Power BI, metadata inconsistencies often arise due to differences in how each platform handles:
Calculated fields (Tableau) vs. Measures and Columns (Power BI)
Data lineage tracking
Connection methods and source queries
Terminology and object references
Without careful planning, you may encounter broken dependencies, duplicate definitions, or unclear data ownership post-migration. This makes establishing a robust metadata management framework in Power BI essential.
Best Practices for Metadata Management in Power BI
1. Centralize with Dataflows and Shared Datasets Post-migration, use Power BI Dataflows to centralize ETL processes and preserve metadata integrity. Dataflows allow teams to reuse cleaned data models and ensure consistent definitions across reports and dashboards.
2. Adopt a Business Glossary Rebuild or migrate your business glossary from Tableau into Power BI documentation layers using tools like Power BI data dictionary exports, documentation templates, or integrations with Microsoft Purview. This ensures end users interpret KPIs and metrics consistently.
3. Use Lineage View and Impact Analysis Leverage lineage view in Power BI Service to trace data from source to dashboard. This feature is essential for auditing changes, understanding data dependencies, and reducing risks during updates.
4. Implement Role-Based Access Controls (RBAC) Metadata often contains sensitive definitions and transformation logic. Assign role-based permissions to ensure only authorized users can access or edit core dataset metadata.
5. Automate Metadata Documentation Tools like Tabular Editor, DAX Studio, or PowerShell scripts can help export and document Power BI metadata programmatically. Automating this process ensures your metadata stays up to date even as models evolve.
The OfficeSolution Advantage
At OfficeSolution, we support enterprises throughout the entire migration journey—from visual rebuilds to metadata realignment. With our deep expertise in both Tableau and Power BI ecosystems, we ensure that your metadata remains a strong foundation for reporting accuracy and governance.
Explore more migration best practices and tools at 🔗 https://tableautopowerbimigration.com/
Conclusion Metadata management is not just an IT concern—it’s central to trust, performance, and decision-making in Power BI. Post-migration success depends on aligning metadata strategies with Power BI’s architecture and features. By investing in metadata governance now, businesses can avoid reporting pitfalls and unlock more scalable insights in the future.
0 notes
Text
Easy Way to Pass AZ-900 Exam on First Attempt
Passing the Microsoft Azure Fundamentals (AZ-900) exam on your first try is absolutely achievable — if you follow the right strategy. Whether you're new to cloud computing or brushing up on your basics, these expert tips will help you prepare efficiently and confidently.
1. Know the Exam Blueprint Inside Out
Start by understanding what the exam covers. Microsoft categorizes the exam into major areas such as:
Cloud Concepts
Core Azure Services
Azure Governance and Compliance
Azure Pricing, SLA, and Lifecycle
👉 Tip: Use Microsoft Learn to study each topic clearly.
2. Use Free Learning Paths on Microsoft Learn
Microsoft’s official learning path is completely free and covers the full exam syllabus in a beginner-friendly manner. It includes modules, knowledge checks, and interactive content.
3. Practice Smart with Trusted Resources
Practice is key — but only when it comes from reliable platforms.
✅ ClearCatNet offers realistic AZ-900 practice tests, flashcards, and cheat sheets tailored to the latest exam format.
✅ JobExamPrep provides topic-wise quizzes, exam simulators, and timed tests to build your confidence and speed.
These platforms are updated regularly and perfect for real-world exam prep. 4. Focus on Core Concepts — Not Just Memorization
Understand key terms like:
IaaS vs. PaaS vs. SaaS
Azure regions, availability zones
Cost management and billing
Role-Based Access Control (RBAC)
A deep understanding of these concepts is more helpful than rote learning.
5. Reinforce Learning with Visuals & Flashcards
Use visual tools and flashcards to quickly revise:
Azure service icons
Core cloud models
Azure CLI vs. PowerShell differences
Flashcards from ClearCatNet are especially useful for quick daily review.
6. Simulate the Real Exam Environment
Time-bound mock tests from JobExamPrep will train you to manage the 60-minute exam window efficiently. Always aim for 90%+ consistently before booking the actual test.
7. Revise Smartly Before the Exam
Revisit:
All summary notes from Microsoft Learn
Quick review sections from JobExamPrep
Cheat sheets on ClearCatNet
Keep your last few days stress-free with focused revision, not new topics.Final Tip: Confidence Comes with Practice
The AZ-900 exam is designed for beginners. If you follow structured learning and practice sincerely with platforms like ClearCatNet and JobExamPrep, you’ll pass on your first try with ease.
Click here to Start Exam
Click here to Download PDF
0 notes
Text
Unlocking the Full Potential of iManage: PowerShell, Law Firms, Records, and More
In today’s fast-paced legal and business environment, efficiency and secure document management are critical. That's where iManage steps in—a leading platform that empowers law firms and businesses to manage documents, emails, records, and workflows with precision. As an official partner, MacroAgility Inc. specializes in implementing iManage solutions tailored to meet unique business needs.
Let’s explore how iManage is transforming the landscape for law firms and enterprises alike, touching on key areas such as iManage PowerShell, iManage Records, iManage Law Firms LLC, and more.
iManage PowerShell: Automation Made Simple
For IT teams and system administrators, iManage PowerShell provides a powerful scripting environment to automate repetitive tasks, streamline user management, and enhance system performance. From onboarding new users to managing workspaces and document security, PowerShell scripting reduces manual workload and minimizes human error.
MacroAgility Inc. offers support and consultancy for businesses looking to integrate iManage PowerShell scripts into their existing infrastructure, ensuring a seamless and optimized deployment.
iManage News: Staying Ahead of the Curve
The world of document management is always evolving. On MacroAgility’s News & Events page, you can stay updated on the latest developments in iManage technology, new product features, and major industry updates. Whether it’s cloud migrations, security upgrades, or AI-enhanced document search functionalities, staying informed helps your firm remain competitive and secure.
iManage Records: Compliance and Control
Maintaining regulatory compliance while managing sensitive records is no easy feat. iManage Records is a robust solution for electronic and physical records management, offering lifecycle governance to ensure nothing falls through the cracks.
MacroAgility Inc. provides consultation for iManage Records implementation, helping clients maintain audit trails, retention policies, and defensible compliance—all within a single platform.
iManage Law Firms: Empowering Legal Workflows
Legal professionals face immense pressure to deliver timely and accurate results. iManage for law firms enhances productivity by centralizing content management, improving collaboration, and ensuring data security. Features like version control, full-text search, and secure client sharing make it a must-have for modern legal practices.
At MacroAgility Inc., our consultants work closely with law firms to customize iManage configurations that align with specific practice areas and internal workflows.
iManage Work: The Core of Productivity
The flagship product, iManage Work, is the heart of the iManage suite. It unifies documents, emails, and communications in a single intuitive interface. Users can quickly access files, collaborate on projects, and manage tasks—all while ensuring compliance and security.
MacroAgility’s iManage Work consultants offer implementation, training, and post-launch support to help you extract maximum value from the platform.
iManage Reviews: What the Experts Say
Customer and expert iManage reviews consistently praise the platform’s usability, security, and customization options. From small firms to global enterprises, users highlight how iManage has improved their productivity and streamlined document workflows.
MacroAgility’s client testimonials reinforce this sentiment, showcasing successful deployments across various sectors. Their deep understanding of iManage solutions ensures that each project meets or exceeds expectations.
iManage Business Banking: Secure Document Management
In the financial sector, iManage for business banking is gaining traction. Financial institutions use the platform to manage client documentation, loan records, and compliance files with ease and security.
MacroAgility works with financial firms to implement iManage in a way that meets strict industry standards and regulations, ensuring both performance and peace of mind.
iManage Law Firms LLC: Custom Solutions for Specialized Needs
iManage Law Firms LLC and similar legal entities benefit from tailored iManage deployments that address unique operational challenges. Whether you're a boutique law firm or a multi-office practice, iManage offers the flexibility to scale and adapt.
MacroAgility Inc. stands out as a trusted partner, delivering industry-specific solutions that enhance efficiency, security, and client service.
Conclusion
Whether you're a law firm, financial institution, or enterprise in need of robust document management, iManage—when implemented by experts like MacroAgility Inc.—delivers exceptional results. From automation with PowerShell to compliance with records management, iManage is more than just software—it’s a smarter way to work.
#imanage powershell#imanage news#imanage records#imanage law firms#imanage work#imanage reviews#imanage business banking#imanage law firms llc
0 notes
Text
Future-Proof Your IT Career with TechshilaMind’s Active Directory Administrator Course
In today’s enterprise environments, managing users, securing data, and controlling access are mission-critical responsibilities. If you're looking to become an essential part of any organization's IT backbone, Active Directory (AD) mastery is non-negotiable.
At TechshilaMind, the Active Directory Administrator course is crafted by experts to ensure you're ready to lead in these areas with confidence and skill.
What is Active Directory? Why Should You Learn It?
Active Directory is Microsoft's identity and access management service used by 90%+ of Fortune 1000 companies. It serves as a centralized system for:
User Authentication
Network Resource Management
Security Policy Enforcement
Learning AD helps you understand the core of enterprise-level infrastructure and positions you as a valuable asset in roles such as:
System Administrator
Network Administrator
IT Support Engineer
Security Analyst
Explore how this technology can elevate your IT skill set in the Active Directory Administrator course.
In-Depth Course Curriculum Highlights
The course is structured to ensure clarity and progression – from basic to expert-level competencies:
Module 1: Introduction to Active Directory
What is AD?
Architecture and Components
AD vs Azure AD
Module 2: Setting Up Domain Controllers
Installing and Configuring ADDS
DNS Integration
Creating Domains and Forests
Module 3: User and Group Management
OU (Organizational Unit) Structure
Managing Users, Groups, and Computers
Scripting with PowerShell
Module 4: Group Policy Objects (GPOs)
What are GPOs?
Creating and Linking GPOs
Group Policy Troubleshooting
Module 5: Security, Backup, and Recovery
AD Security Best Practices
Implementing Role-Based Access Control
AD Backup, Restore, and Disaster Recovery
Module 6: Real-Time Case Studies & Project Work
Industry Use Cases
Hands-On Assignments
Simulated Scenarios
Download the full syllabus by visiting the course page.
Who Should Join This Course?
Whether you're starting from scratch or polishing your skills, this course suits:
Fresh IT graduates seeking a powerful niche
System Admins upgrading their skillset
Cybersecurity professionals needing infrastructure knowledge
Tech leads and managers exploring AD deployment at scale
Key Features That Set This Course Apart
✅ Live Instructor-Led Sessions ✅ 24/7 Dedicated Mentor Support ✅ Interview Prep + Career Mentorship ✅ Flexible Weekday & Weekend Schedules ✅ Access to LMS + Recorded Lectures ✅ Official Certification Preparation
What You Can Expect After Completion
Job-Ready Skills to handle Active Directory infrastructure
Certification-ready preparation for roles such as MCSA, Microsoft Certified: Azure Administrator Associate
Boosted Employability with in-demand tools like PowerShell, GPO, LDAP
Get started now: Join the Active Directory Administrator course today
Still Have Questions?
Contact TechshilaMind directly for a free consultation:
📞 +91-7505974183
What Students Are Saying
⭐⭐⭐⭐⭐ “The instructors are highly knowledgeable, and I loved how real-time projects were part of the learning. Definitely worth the investment!” — Amit Sharma, Network Engineer
⭐⭐⭐⭐ “Perfect for those trying to break into infrastructure roles. Their career support was the cherry on top.” — Nisha R., System Admin Intern
Your Path to Becoming an AD Expert Starts Here
If you've been looking for a well-structured, job-oriented course that delivers not just knowledge but career impact, then the Active Directory Administrator course from TechshilaMind is your launchpad.
0 notes
Text
System Administration Online Course: Master Modern IT with Gritty Tech
In today’s digitally driven world, efficient system management is critical for any business. A comprehensive System administration online course equips learners with the skills required to handle system networks, servers, security protocols, and more. Whether you’re aiming for a career upgrade or starting fresh in the tech field, and flexible learning experience For More…

Why Choose Gritty Tech for Your System Administration Online Course?
Top-Quality Education, Affordable Price
Gritty Tech stands out in the education sector for delivering high-quality learning at affordable rates. Our System administration online course is designed to provide exceptional training in core IT administration areas without overburdening your budget.
Global Tutor Network Spanning 110+ Countries
We bring together expert instructors from around the world. With a diverse team of seasoned professionals, Gritty Tech ensures your System administration online course is led by industry veterans with practical experience in managing modern infrastructure.
Flexible Payment and Satisfaction Policies
Learners can benefit from our monthly and session-wise payment models. We also offer an easy refund policy and tutor replacement options, reinforcing our commitment to student satisfaction. Our System administration online course is built around your needs.
What You Will Learn in the System Administration Online Course
Gritty Tech’s curriculum covers every key aspect needed to become a proficient system administrator. With real-world scenarios and hands-on labs, the course includes:
Linux and Windows server installation and configuration
Network architecture, monitoring, and troubleshooting
Security controls, firewalls, and user permissions
Data backup, system recovery, and storage solutions
Cloud platforms introduction and server virtualization
Task automation using scripting (Bash, PowerShell)
Managing Active Directory and DNS configurations
Each module in the System administration online course builds foundational expertise, reinforced by real-time assignments.
Who Should Take This Course
The System administration online course is ideal for:
Beginners entering the IT field
IT professionals aiming to upskill
Computer science students
Freelancers and consultants supporting IT operations
System engineers seeking certification
Career Paths After Completing the System Administration Online Course
With a solid foundation from our System administration online course, students can pursue rewarding roles such as:
System Administrator
IT Support Technician
Network Engineer
Cloud Operations Associate
DevOps Engineer
Server Security Analyst
Companies across industries depend on skilled system administrators to maintain robust and secure IT environments.
What Makes the Gritty Tech System Administration Online Course Stand Out
Experienced Tutors
Gritty Tech tutors are not just educators—they are working professionals with hands-on experience in systems management. Their real-world insights enhance the quality of your System administration online course journey.
Hands-On Projects and Labs
You will work with actual server environments and practice live configurations. These exercises provide a practical layer to your theoretical learning.
Interactive and Self-Paced
The System administration online course can be completed at your convenience. Whether you study full-time or part-time, the flexibility is built-in to support your schedule.
Certification Included
After successful completion of your System administration online course, you’ll receive a digital certificate from Gritty Tech, which you can share with potential employers or on professional platforms.
Real Student Support
From one-on-one mentoring to peer support, our System administration online course ensures you never feel isolated. Our global community provides an excellent platform for collaboration and discussion.
Related Topics Covered in the Course
The course doesn’t stop at systems. To help broaden your technical base, we integrate related training on:
Linux system administration
Windows server roles
Cloud administration fundamentals
Networking essentials
Cybersecurity basics
IT support workflows
Infrastructure monitoring tools
These modules complement the core lessons of the System administration online course, helping you become a versatile IT professional.
10 Most Asked Questions About the System Administration Online Course
What is a system administration online course?
A System administration online course teaches the principles and practices of managing IT systems and networks remotely via an interactive online format.
Who should take the system administration online course?
Anyone seeking a career in IT, especially those interested in maintaining servers, networks, and databases, should consider a System administration online course.
What will I learn in the system administration online course?
You’ll gain expertise in system configuration, network setup, user management, and IT troubleshooting through our System administration online course.
Is prior IT experience required for the system administration online course?
No prior experience is needed. The System administration online course is suitable for both beginners and intermediate learners.
How long is the system administration online course?
Most students complete the System administration online course within 6 to 10 weeks depending on their pace.
Does Gritty Tech provide certification after the course?
Yes, a verified certificate is awarded upon completing the System administration online course.
What tools are used in the system administration online course?
You’ll work with Linux, Windows Server, VMware, PowerShell, and various network monitoring tools during the System administration online course.
Can I change my tutor during the course?
Yes. We offer flexible tutor replacement options during your System administration online course.
What if I’m not satisfied with the course?
Gritty Tech provides an easy refund policy for learners who are unsatisfied with their System administration online course experience.
Can I pay in installments for the system administration online course?
Absolutely. We support monthly and session-wise payment plans to make the System administration online course more accessible.
Conclusion
Gritty Tech’s System administration online course is a comprehensive, flexible, and industry-relevant program that prepares you for success in IT systems management. With world-class tutors, real-time labs, affordable pricing, and a globally recognized certificate, you get everything you need to transform your career.
Whether you’re starting out or advancing in your IT journey, this System administration online course is your launchpad. Take the first step today and join a learning community that spans over 110 countries. Gritty Tech makes tech education not only possible—but powerful.
0 notes
Text
Enhancing Cybersecurity Resilience
Discover how a modern Threat Intelligence Platform empowers organizations with actionable insights, proactive defense, and next-gen cybersecurity capabilities.
In the ever-evolving digital world, cybersecurity threats have grown in complexity, frequency, and scale. From ransomware and phishing attacks to data breaches and nation-state cyber espionage, the digital threat landscape has expanded into a vast, dynamic battlefield. For organizations aiming to remain secure, simply reacting to threats after they happen is no longer a viable option.

Today, security teams must be proactive, predictive, and precise in their threat response strategies. This is where a Threat Intelligence Platform (TIP) plays a vital role. Rather than operating in silos or relying solely on isolated security tools, a modern TIP serves as a centralized hub for collecting, analyzing, and distributing threat data in real-time—empowering cybersecurity professionals to make informed decisions faster.
In this article, we delve deep into what makes a Threat Intelligence Platform essential in the modern age, how it integrates with other security protocols, and why forward-looking organizations are investing in it to build stronger cyber defenses.
Understanding the Role of a Threat Intelligence Platform
A Threat Intelligence Platform is not just another security tool—it is a strategic asset. It aggregates threat data from multiple sources, correlates information, and offers context-rich insights that help in identifying and mitigating cyber threats before they manifest into breaches.
The core functions of a TIP include:
Data Aggregation: Collects structured and unstructured threat data from external feeds, internal systems, and global cybersecurity communities.
Analysis and Correlation: Uses advanced algorithms, machine learning, and contextual linking to correlate data points across diverse threat vectors.
Threat Prioritization: Automatically ranks threats based on relevance, severity, and business impact.
Actionable Intelligence Delivery: Integrates with SIEMs, firewalls, and incident response platforms to deliver real-time alerts and automated response actions.
Ultimately, a TIP transforms raw data into actionable threat intelligence, reducing the burden on security analysts and enabling faster incident detection and response.
The Increasing Complexity of the Cyber Threat Landscape
Cybercriminals today use sophisticated methods to infiltrate networks. Techniques like spear-phishing, zero-day exploits, and AI-driven malware are growing in prevalence. Furthermore, the lines between criminal groups, hacktivists, and nation-state actors are increasingly blurred, adding layers of complexity.
Key trends include:
Multi-Stage Attacks: Attackers often use a chain of exploits to gain access and maintain persistence in a system.
Supply Chain Threats: Vendors and third-party providers are now frequent targets, becoming indirect entry points.
Living-off-the-Land Attacks: Cybercriminals use legitimate tools (e.g., PowerShell, Windows Management Instrumentation) to avoid detection.
To counter such tactics, organizations need visibility not just within their internal environments but across the global threat ecosystem. This is where the strategic advantage of a TIP comes into play.
Features of an Effective Threat Intelligence Platform
Not all TIPs are created equal. The most effective platforms provide a range of features that enhance detection, analysis, and response:
1. Automated Data Collection
A TIP should automatically collect data from various threat feeds, security logs, dark web sources, and open databases. Automation reduces manual workload and ensures real-time threat visibility.
2. Advanced Threat Correlation
The platform must be capable of correlating indicators of compromise (IOCs) such as IP addresses, file hashes, domain names, and malware signatures across different incidents to uncover patterns.

3. Integration with Security Ecosystems
A TIP that integrates with SIEM, SOAR, EDR, and firewall solutions ensures that insights are not siloed but can trigger immediate security actions.
4. Contextual Threat Enrichment
Context is key. The TIP should enrich threat data with geographical, behavioral, and historical insights to aid faster and more accurate decision-making.
5. Collaborative Intelligence Sharing
Sharing threat intelligence across industry groups, ISACs, and global cyber communities strengthens collective security.
Use Case: Proactive Defense in Financial Services
Financial institutions are a prime target for cybercriminals due to the high-value data they hold. Let’s consider a mid-size bank integrating a TIP into its security framework.
Scenario:
A suspicious domain is flagged on a global threat feed. The TIP correlates this IOC with phishing attempts targeting banking customers in Asia. Upon further analysis, the platform uncovers malware strains associated with credential theft. The platform alerts the SOC (Security Operations Center) and triggers automated rules to block the domain at the firewall level.
This real-time detection and action, driven by the TIP, prevents a potential breach and demonstrates how actionable intelligence can drastically reduce incident response time and damage.
How TIPs Leverage Open-Source Intelligence (OSINT)
Open-Source Intelligence (OSINT) refers to data collected from publicly available sources such as news reports, forums, blogs, social media, code repositories, and more. When integrated with a Threat Intelligence Platform, OSINT enhances the scope and depth of intelligence gathering.
For example, attackers often discuss vulnerabilities or leak data on underground forums. A TIP that harvests OSINT can pick up on these signals early, offering preemptive insights before the threat becomes widespread.
Additionally, by analyzing chatter patterns, sentiment, and keywords, TIPs can identify emerging attack vectors or vulnerable sectors—enabling organizations to prepare in advance.
The Power of Cyber Threat Analysis in TIPs
Cyber Threat Analysis is the heart of any effective threat intelligence strategy. A TIP streamlines this process by offering analytics dashboards, pattern recognition engines, and predictive modeling tools. It breaks down raw data into:
Tactics, Techniques, and Procedures (TTPs) of attackers.
Attack timelines and kill chain mapping.
Threat actor attribution based on behavior and tools used.
This deep analysis enables security teams to distinguish between random noise and real threats, reducing alert fatigue and boosting operational efficiency.
Moreover, advanced platforms use AI and machine learning to improve over time, identifying new threat variants and behavioral patterns that may otherwise go unnoticed.
Importance of Digital Risk Protection in TIP Integration
Today’s attack surfaces extend beyond corporate firewalls. Executives, employees, vendors, and third-party platforms create a digital footprint that’s often unmonitored. This is where Digital Risk Protection (DRP) comes into play.

By integrating DRP capabilities into a TIP, organizations gain visibility into:
Brand impersonation attempts.
Leaked credentials on the dark web.
Domain spoofing and phishing sites.
Social media threats and impersonation.
This holistic visibility allows organizations to safeguard their brand reputation, intellectual property, and customer trust more effectively.
Threat Intelligence Platform Deployment: Challenges and Solutions
While the advantages of TIPs are compelling, implementing them does come with challenges. Let’s explore a few and how organizations can address them:
1. Data Overload
Many TIPs collect vast amounts of data, which can become overwhelming. The solution lies in deploying machine learning filters and customizable threat scoring models to highlight what matters most.
2. False Positives
Too many false positives can waste time and resources. A TIP with behavior-based analysis and contextual enrichment significantly reduces such noise.
3. Integration Issues
Legacy systems might not integrate well with newer TIPs. Opt for platforms with strong API support and modular architecture for smoother interoperability.
4. Skilled Workforce
Threat intelligence requires expertise. While TIPs automate many functions, upskilling teams and investing in regular training ensures that organizations derive maximum value from their platforms.
Future of Threat Intelligence Platforms
With the increasing digitization of services and rise in remote work, the importance of real-time, predictive cybersecurity has never been greater. The future of TIPs lies in:
AI-Driven Threat Prediction: Using neural networks and behavioral analytics to forecast threats before they manifest.
Cloud-Native Architecture: Offering scalable, elastic intelligence solutions for hybrid and cloud-native enterprises.
Blockchain for Threat Data Integrity: Ensuring the immutability and trustworthiness of shared intelligence.
Global Threat Intelligence Sharing Consortiums: Encouraging collective intelligence sharing to counter global threats collaboratively.
Organizations that invest early in TIPs are setting themselves up for long-term resilience and competitiveness.
Conclusion
In an age where cyber threats evolve by the minute, waiting for an incident to happen is no longer a luxury any organization can afford. A modern Threat Intelligence Platform doesn’t just help organizations react—it equips them to anticipate, prepare, and act swiftly.
From aggregating data to conducting in-depth Cyber Threat Analysis, from tapping into Open-Source Intelligence (OSINT) to enhancing Digital Risk Protection, a TIP acts as a central nervous system for proactive cybersecurity defense.
At DeXpose, we believe in empowering enterprises with cutting-edge threat intelligence solutions. Our mission is to help businesses stay a step ahead of adversaries by providing tools and insights that foster cyber resilience.
Are you ready to strengthen your organization’s cyber defense posture? Reach out to DeXpose today and explore how our intelligence-driven solutions can transform your approach to cybersecurity.
0 notes
Text
Senior Platform Engineer (PowerShell and Bash)
with .NET (legacy, Core), JavaScript (legacy frameworks, React, Node) and Golang systems. Scripting using a language… Apply Now
0 notes
Text
Certified DevSecOps Professional: Career Path, Salary & Skills
Introduction
As the demand for secure, agile software development continues to rise, the role of a Certified DevSecOps Professional has become critical in modern IT environments. Organizations today are rapidly adopting DevSecOps to shift security left in the software development lifecycle. This shift means security is no longer an afterthought—it is integrated from the beginning. Whether you're just exploring the DevSecOps tutorial for beginners or looking to level up with a professional certification, understanding the career landscape, salary potential, and required skills can help you plan your next move.
This comprehensive guide explores the journey of becoming a Certified DevSecOps Professional, the skills you'll need, the career opportunities available, and the average salary you can expect. Let’s dive into the practical and professional aspects that make DevSecOps one of the most in-demand IT specialties in 2025 and beyond.
What Is DevSecOps?
Integrating Security into DevOps
DevSecOps is the practice of integrating security into every phase of the DevOps pipeline. Traditional security processes often occur at the end of development, leading to delays and vulnerabilities. DevSecOps introduces security checks early in development, making applications more secure and compliant from the start.
The Goal of DevSecOps
The ultimate goal is to create a culture where development, security, and operations teams collaborate to deliver secure and high-quality software faster. DevSecOps emphasizes automation, continuous integration, continuous delivery (CI/CD), and proactive risk management.
Why Choose a Career as a Certified DevSecOps Professional?
High Demand and Job Security
The need for DevSecOps professionals is growing fast. According to a Cybersecurity Ventures report, there will be 3.5 million unfilled cybersecurity jobs globally by 2025. Many of these roles demand DevSecOps expertise.
Lucrative Salary Packages
Because of the specialized skill set required, DevSecOps professionals are among the highest-paid tech roles. Salaries can range from $110,000 to $180,000 annually depending on experience, location, and industry.
Career Versatility
This role opens up diverse paths such as:
Application Security Engineer
DevSecOps Architect
Cloud Security Engineer
Security Automation Engineer
Roles and Responsibilities of a DevSecOps Professional
Core Responsibilities
Integrate security tools and practices into CI/CD pipelines
Perform threat modeling and vulnerability scanning
Automate compliance and security policies
Conduct security code reviews
Monitor runtime environments for suspicious activities
Collaboration
A Certified DevSecOps Professional acts as a bridge between development, operations, and security teams. Strong communication skills are crucial to ensure secure, efficient, and fast software delivery.
Skills Required to Become a Certified DevSecOps Professional
Technical Skills
Scripting Languages: Bash, Python, or PowerShell
Configuration Management: Ansible, Chef, or Puppet
CI/CD Tools: Jenkins, GitLab CI, CircleCI
Containerization: Docker, Kubernetes
Security Tools: SonarQube, Checkmarx, OWASP ZAP, Aqua Security
Cloud Platforms: AWS, Azure, Google Cloud
Soft Skills
Problem-solving
Collaboration
Communication
Time Management
DevSecOps Tutorial for Beginners: A Step-by-Step Guide
Step 1: Understand the Basics of DevOps
Before diving into DevSecOps, make sure you're clear on DevOps principles, including CI/CD, infrastructure as code, and agile development.
Step 2: Learn Security Fundamentals
Study foundational cybersecurity concepts like threat modeling, encryption, authentication, and access control.
Step 3: Get Hands-On With Tools
Use open-source tools to practice integrating security into DevOps pipelines:
# Example: Running a static analysis scan with SonarQube
sonar-scanner \
-Dsonar.projectKey=myapp \
-Dsonar.sources=. \
-Dsonar.host.url=http://localhost:9000 \
-Dsonar.login=your_token
Step 4: Build Your Own Secure CI/CD Pipeline
Practice creating pipelines with Jenkins or GitLab CI that include steps for:
Static Code Analysis
Dependency Checking
Container Image Scanning
Step 5: Monitor and Respond
Set up tools like Prometheus and Grafana to monitor your applications and detect anomalies.
Certification Paths for DevSecOps
Popular Certifications
Certified DevSecOps Professional
Certified Kubernetes Security Specialist (CKS)
AWS Certified Security - Specialty
GIAC Cloud Security Automation (GCSA)
Exam Topics Typically Include:
Security in CI/CD
Secure Infrastructure as Code
Cloud-native Security Practices
Secure Coding Practices
Salary Outlook for DevSecOps Professionals
Salary by Experience
Entry-Level: $95,000 - $115,000
Mid-Level: $120,000 - $140,000
Senior-Level: $145,000 - $180,000+
Salary by Location
USA: Highest average salaries, especially in tech hubs like San Francisco, Austin, and New York.
India: ₹9 LPA to ₹30+ LPA depending on experience.
Europe: €70,000 - €120,000 depending on country.
Real-World Example: How Companies Use DevSecOps
Case Study: DevSecOps at a Fintech Startup
A fintech company integrated DevSecOps tools like Snyk, Jenkins, and Kubernetes to secure their microservices architecture. They reduced vulnerabilities by 60% in just three months while speeding up deployments by 40%.
Key Takeaways
Early threat detection saves time and cost
Automated pipelines improve consistency and compliance
Developers take ownership of code security
Challenges in DevSecOps and How to Overcome Them
Cultural Resistance
Solution: Conduct training and workshops to foster collaboration between teams.
Tool Integration
Solution: Choose tools that support REST APIs and offer strong documentation.
Skill Gaps
Solution: Continuous learning and upskilling through real-world projects and sandbox environments.
Career Roadmap: From Beginner to Expert
Beginner Level
Understand DevSecOps concepts
Explore basic tools and scripting
Start with a DevSecOps tutorial for beginners
Intermediate Level
Build and manage secure CI/CD pipelines
Gain practical experience with container security and cloud security
Advanced Level
Architect secure cloud infrastructure
Lead DevSecOps adoption in organizations
Mentor junior engineers
Conclusion
The future of software development is secure, agile, and automated—and that means DevSecOps. Becoming a Certified DevSecOps Professional offers not only job security and high salaries but also the chance to play a vital role in creating safer digital ecosystems. Whether you’re following a DevSecOps tutorial for beginners or advancing into certification prep, this career path is both rewarding and future-proof.
Take the first step today: Start learning, start practicing, and aim for certification!
1 note
·
View note
Text
Boost Your Fortnite FPS in 2025: The Complete Optimization Guide
youtube
Unlock Maximum Fortnite FPS in 2025: Pro Settings & Hidden Tweaks Revealed
In 2025, achieving peak performance in Fortnite requires more than just powerful hardware. Even the most expensive gaming setups can struggle with inconsistent frame rates and input lag if the system isn’t properly optimized. This guide is designed for players who want to push their system to its limits — without spending more money. Whether you’re a competitive player or just want smoother gameplay, this comprehensive Fortnite optimization guide will walk you through the best tools and settings to significantly boost FPS, reduce input lag, and create a seamless experience.
From built-in Windows adjustments to game-specific software like Razer Cortex and AMD Adrenalin, we’ll break down each step in a clear, actionable format. Our goal is to help you reach 240+ FPS with ease and consistency, using only free tools and smart configuration choices.
Check System Resource Usage First
Before making any deep optimizations, it’s crucial to understand how your PC is currently handling resource allocation. Begin by opening Task Manager (Ctrl + Alt + Delete > Task Manager). Under the Processes tab, review which applications are consuming the most CPU and memory.
Close unused applications like web browsers or VPN services, which often run in the background and consume RAM.
Navigate to the Performance tab to verify that your CPU is operating at its intended base speed.
Confirm that your memory (RAM) is running at its advertised frequency. If it’s not, you may need to enable XMP in your BIOS.

Avoid Complex Scripts — Use Razer Cortex Instead
While there are command-line based options like Windows 10 Debloater (DBLO), they often require technical knowledge and manual PowerShell scripts. For a user-friendly alternative, consider Razer Cortex — a free tool that automates performance tuning with just a few clicks.
Here’s how to use it:
Download and install Razer Cortex.
Open the application and go to the Booster tab.
Enable all core options such as:
Disable CPU Sleep Mode
Enable Game Power Solutions
Clear Clipboard and Clean RAM
Disable Sticky Keys, Cortana, Telemetry, and Error Reporting

Use Razer Cortex Speed Optimization Features
After setting up the Booster functions, move on to the Speed Up section of Razer Cortex. This tool scans your PC for services and processes that can be safely disabled or paused to improve overall system responsiveness.
Steps to follow:
Click Optimize Now under the Speed Up tab.
Let Cortex analyze and adjust unnecessary background activities.
This process will reduce system load, freeing resources for Fortnite and other games.
You’ll also find the Booster Prime feature under the same application, allowing game-specific tweaks. For Fortnite, it lets you pick from performance-focused or quality-based settings depending on your needs.
Optimize Fortnite Graphics Settings via Booster Prime
With Booster Prime, users can apply recommended Fortnite settings without navigating the in-game menu. This simplifies the optimization process, especially for players not familiar with technical configuration.
Key settings to configure:
Resolution: Stick with native (1920x1080 for most) or drop slightly for extra performance.
Display Mode: Use Windowed Fullscreen for better compatibility with overlays and task switching.
Graphics Profile: Choose Performance Mode to prioritize FPS over visuals, or Balanced for a mix of both.
Once settings are chosen, click Optimize, and Razer Cortex will apply all changes automatically. You’ll see increased FPS and reduced stuttering almost immediately.
Track Resource Gains and Performance Impact
Once you’ve applied Razer Cortex optimizations, monitor the system changes in real-time. The software displays how much RAM is freed and which services have been stopped.
For example:
You might see 3–4 GB of RAM released, depending on how many background applications were disabled.
Services like Cortana and telemetry often consume hidden resources — disabling them can free both memory and CPU cycles.

Enable AMD Adrenalin Performance Settings (For AMD Users)
If your system is powered by an AMD GPU, the Adrenalin Software Suite offers multiple settings that improve gaming performance with minimal setup.
Recommended options to enable:
Anti-Lag: Reduces input latency, making your controls feel more immediate.
Radeon Super Resolution: Upscales games to provide smoother performance at lower system loads.
Enhanced Sync: Improves frame pacing without the drawbacks of traditional V-Sync.
Image Sharpening: Adds clarity without a major hit to performance.
Radeon Boost: Dynamically lowers resolution during fast motion to maintain smooth FPS.
Be sure to enable Borderless Fullscreen in your game settings for optimal GPU performance and lower system latency.
Match Frame Rate with Monitor Refresh Rate
One of the simplest and most effective ways to improve both performance and gameplay experience is to cap your frame rate to match your monitor’s refresh rate. For instance, if you’re using a 240Hz monitor, setting Fortnite’s max FPS to 240 will reduce unnecessary GPU strain and maintain stable frame pacing.
Benefits of FPS capping:
Lower input latency
Reduced screen tearing
Better thermals and power efficiency
This adjustment ensures your system isn’t overworking when there’s no benefit, which can lead to more stable and predictable gameplay — especially during extended play sessions.
Real-World Performance Comparison
After applying Razer Cortex and configuring system settings, players often see dramatic performance improvements. In test environments using a 2K resolution on DirectX 12, systems previously capped at 50–60 FPS with 15–20 ms response times jumped to 170–180 FPS with a 3–5 ms response time.
When switching to 1080p resolution:
Frame rates typically exceed 200 FPS
Reduced frame time results in smoother aiming and lower delay
Competitive advantage improves due to lower latency and higher visual consistency
These results are reproducible on most modern gaming rigs, regardless of brand, as long as the system has adequate hardware and is properly optimized.
Switch Between Performance Modes for Different Games
One of Razer Cortex’s strongest features is its flexibility. You can easily switch between optimization profiles depending on the type of game you’re playing. For Fortnite, choose high-performance settings to prioritize responsiveness and frame rate. But for visually rich, story-driven games, you might want higher quality visuals.
Using Booster Prime:
Choose your desired game from the list.
Select a profile such as Performance, Balanced, or Quality.
Apply settings instantly by clicking Optimize, then launch the game directly.
This quick toggle capability makes it easy to adapt your system to different gaming needs without having to manually change settings every time.
Final Performance Test: Fortnite in 2K with Performance Mode
To push your system to the limit, test Fortnite under 2K resolution and Performance Mode enabled. Without any optimizations, many systems may average 140–160 FPS. However, with all the Razer Cortex and system tweaks applied:
Frame rates can spike above 400 FPS
Input delay and frame time reduce significantly
Gameplay becomes smoother and more responsive, ideal for fast-paced shooters

Conclusion: Unlock Peak Fortnite Performance in 2025
Optimizing Fortnite for maximum FPS and minimal input lag doesn’t require expensive upgrades or advanced technical skills. With the help of tools like Razer Cortex and AMD Adrenalin, along with proper system tuning, you can dramatically enhance your gameplay experience.
Key takeaways:
Monitor and free system resources using Task Manager
Use Razer Cortex to automate performance boosts with one click
Apply optimized settings for Fortnite via Booster Prime
Match FPS to your monitor’s refresh rate for smoother visuals
Take advantage of GPU-specific software like AMD Adrenalin
Customize settings for performance or quality based on your gaming style
By following this fortnite optimization guide, you can achieve a consistent fortnite fps boost in 2025 while also reducing input lag and ensuring your system runs at peak performance. These steps are applicable not only to Fortnite but to nearly any competitive game you play. It’s time to make your hardware work smarter — not harder.
🎮 Level 99 Kitchen Conjurer | Crafting epic culinary quests where every dish is a legendary drop. Wielding spatulas and controllers with equal mastery, I’m here to guide you through recipes that give +10 to flavor and +5 to happiness. Join my party as we raid the kitchen and unlock achievement-worthy meals! 🍳✨ #GamingChef #CulinaryQuests
For More, Visit @https://haplogamingcook.com
#fortnite fps guide 2025#increase fortnite fps#fortnite performance optimization#fortnite fps boost settings#fortnite graphics settings#best fortnite settings for fps#fortnite lag fix#fortnite fps drops fix#fortnite competitive settings#fortnite performance mode#fortnite pc optimization#fortnite fps boost tips#fortnite low end pc settings#fortnite high fps config#fortnite graphics optimization#fortnite game optimization#fortnite fps unlock#fortnite performance guide#fortnite settings guide 2025#fortnite competitive fps#Youtube
0 notes
Text
Top Function as a Service (FaaS) Vendors of 2025
Businesses encounter obstacles in implementing effective and scalable development processes. Traditional techniques frequently fail to meet the growing expectations for speed, scalability, and innovation. That's where Function as a Service comes in.
FaaS is more than another addition to the technological stack; it marks a paradigm shift in how applications are created and delivered. It provides a serverless computing approach that abstracts infrastructure issues, freeing organizations to focus on innovation and core product development. As a result, FaaS has received widespread interest and acceptance in multiple industries, including BFSI, IT & Telecom, Public Sector, Healthcare, and others.
So, what makes FaaS so appealing to corporate leaders? Its value offer is based on the capacity to accelerate time-to-market and improve development outcomes. FaaS allows companies to prioritize delivering new goods and services to consumers by reducing server maintenance, allowing for flexible scalability, cost optimization, and automatic high availability.
In this blog, we'll explore the meaning of Function as a Service (FaaS) and explain how it works. We will showcase the best function as a service (FaaS) software that enables businesses to reduce time-to-market and streamline development processes.
Download the sample report of Market Share: https://qksgroup.com/download-sample-form/market-share-function-as-a-service-2023-worldwide-5169
What is Function-as-a-Service (FaaS)?
Function-as-a-Service (FaaS), is a cloud computing service that enables developers to create, execute, and manage discrete units of code as individual functions, without the need to oversee the underlying infrastructure. This approach enables developers to focus solely on writing code for their application's specific functions, abstracting away the complexities of infrastructure management associated with developing and deploying microservices applications. With FaaS, developers can write and update small, modular pieces of code, which are designed to respond to specific events or triggers. FaaS is commonly used for building microservices, real-time data processing, and automating workflows. It decreases much of the infrastructure management complexity, making it easier for developers to focus on writing code and delivering functionality. FaaS can power the backend for mobile applications, handling user authentication, data synchronization, and push notifications, among other functions.
How Does Function-as-a-Service (FaaS) Work?
FaaS provides programmers with a framework for responding to events via web apps without managing servers.PaaS infrastructure frequently requires server tasks to continue in the background at all times. In contrast, FaaS infrastructure is often invoiced on demand by the service provider, using an event-based execution methodology.
FaaS functions should be formed to bring out a task in response to an input. Limit the scope of your code, keeping it concise and lightweight, so that functions load and run rapidly. FaaS adds value at the function separation level. If you have fewer functions, you will pay additional costs while maintaining the benefit of function separation. The efficiency and scalability of a function may be enhanced by utilizing fewer libraries. Features, microservices, and long-running services will be used to create comprehensive apps.
Download the sample report of Market Forecast: https://qksgroup.com/download-sample-form/market-forecast-function-as-a-service-2024-2028-worldwide-4685
Top Function-as-a-Service (FaaS) Vendors
Amazon
Amazon announced AWS Lambda in 2014. Since then, it has developed into one of their most valuable offerings. It serves as a framework for Alexa skill development and provides easy access to many of AWS's monitoring tools. Lambda natively supports Java, Go, PowerShell, Node.js, C#, Python, and Ruby code.
Alibaba Functions
Alibaba provides a robust platform for serverless computing. You may deploy and run your code using Alibaba Functions without managing infrastructure or servers. To run your code, computational resources are deployed flexibly and reliably. Dispersed clusters exist in a variety of locations. As a result, if one zone becomes unavailable, Alibaba Function Compute will immediately switch to another instance. Using distributed clusters allows any user from anywhere to execute your code faster. It increases productivity.
Microsoft
Microsoft and Azure compete with Microsoft Azure Functions. It is the biggest FaaS provider for designing and delivering event-driven applications. It is part of the Azure ecosystem and supports several programming languages, including C#, JavaScript, F#, Python, Java, PowerShell, and TypeScript.
Azure Functions provides a more complex programming style built around triggers and bindings. An HTTP-triggered function may read a document from Azure Cosmos DB and deliver a queue message using declarative configuration. The platform supports multiple triggers, including online APIs, scheduled tasks, and services such as Azure Storage, Azure Event Hubs, Twilio for SMS, and SendGrid for email.
Vercel
Vercel Functions offers a FaaS platform optimized for static frontends and serverless functions. It hosts webpages and online apps that install rapidly and expand themselves.
The platform stands out for its straightforward and user-friendly design. When running Node.js, Vercel manages dependencies using a single JSON. Developers may also change the runtime version, memory, and execution parameters. Vercel's dashboard provides monitoring logs for tracking functions and requests.
Key Technologies Powering FaaS and Their Strategic Importance
According to QKS Group and insights from the reports “Market Share: Function as a Service, 2023, Worldwide” and “Market Forecast: Function as a Service, 2024-2028, Worldwide”, organizations around the world are increasingly using Function as a Service (FaaS) platforms to streamline their IT operations, reduce infrastructure costs, and improve overall business agility. Businesses that outsource computational work to cloud service providers can focus on their core capabilities, increase profitability, gain a competitive advantage, and reduce time to market for new apps and services.
Using FaaS platforms necessitates sharing sensitive data with third-party cloud providers, including confidential company information and consumer data. As stated in Market Share: Function as a Service, 2023, Worldwide, this raises worries about data privacy and security, as a breach at the service provider's end might result in the disclosure or theft of crucial data. In an era of escalating cyber threats and severe data security rules, enterprises must recognize and mitigate the risks of using FaaS platforms. Implementing strong security measures and performing frequent risk assessments may assist in guaranteeing that the advantages of FaaS are realized without sacrificing data integrity and confidentiality.
Vendors use terms like serverless computing, microservices, and Function as a Service (FaaS) to describe similar underlying technologies. FaaS solutions simplify infrastructure management, enabling rapid application development, deployment, and scalability. Serverless computing and microservices brake systems into small, independent tasks that can be executed on demand, resulting in greater flexibility and efficiency in application development.
Conclusion
Function as a Service (FaaS) is helping businesses build and run applications more efficiently without worrying about server management. It allows companies to scale as needed, reduce costs, and focus on creating better products and services. As more sectors use FaaS, knowing how it works and selecting the right provider will be critical to keeping ahead in a rapidly altering digital landscape.
Related Reports –
https://qksgroup.com/market-research/market-forecast-function-as-a-service-2024-2028-western-europe-4684
https://qksgroup.com/market-research/market-share-function-as-a-service-2023-western-europe-5168
https://qksgroup.com/market-research/market-forecast-function-as-a-service-2024-2028-usa-4683
https://qksgroup.com/market-research/market-share-function-as-a-service-2023-usa-5167
https://qksgroup.com/market-research/market-forecast-function-as-a-service-2024-2028-middle-east-and-africa-4682
https://qksgroup.com/market-research/market-share-function-as-a-service-2023-middle-east-and-africa-5166
https://qksgroup.com/market-research/market-forecast-function-as-a-service-2024-2028-china-4679
https://qksgroup.com/market-research/market-share-function-as-a-service-2023-china-5163
https://qksgroup.com/market-research/market-forecast-function-as-a-service-2024-2028-asia-excluding-japan-and-china-4676
https://qksgroup.com/market-research/market-share-function-as-a-service-2023-asia-excluding-japan-and-china-5160
0 notes
Text
Locate commands
A cmdlet (pronounced “command-let”) is a compiled command. A cmdlet can be developed in .NET or .NET Core and invoked as a command within PowerShell. Thousands of cmdlets are available in your PowerShell installation. The challenge lies in discovering what the cmdlets are and what they can do for you. Cmdlets are named according to a verb-noun naming standard. This pattern can help you to…
0 notes
Text
GPU Hosting Server Windows By CloudMinnister Technologies
Cloudminister Technologies GPU Hosting Server for Windows
Businesses and developers require more than just conventional hosting solutions in the data-driven world of today. Complex tasks that require high-performance computing capabilities that standard CPUs cannot effectively handle include artificial intelligence (AI), machine learning (ML), and large data processing. Cloudminister Technologies GPU hosting servers can help with this.
We will examine GPU hosting servers on Windows from Cloudminister Technologies' point of view in this comprehensive guide, going over their features, benefits, and reasons for being the best option for your company.
A GPU Hosting Server: What Is It?
A dedicated server with Graphical Processing Units (GPUs) for high-performance parallel computing is known as a GPU hosting server. GPUs can process thousands of jobs at once, in contrast to CPUs, which handle tasks sequentially. They are therefore ideal for applications requiring real-time processing and large-scale data computations.
Cloudminister Technologies provides cutting-edge GPU hosting solutions to companies that deal with:
AI and ML Model Training:- Quick and precise creation of machine learning models.
Data analytics:- It is the rapid processing of large datasets to produce insights that may be put to use.
Video processing and 3D rendering:- fluid rendering for multimedia, animation, and gaming applications.
Blockchain Mining:- Designed with strong GPU capabilities for cryptocurrency mining.
Why Opt for GPU Hosting from Cloudminister Technologies?
1. Hardware with High Performance
The newest NVIDIA and AMD GPUs power the state-of-the-art hardware solutions used by Cloudminister Technologies. Their servers are built to provide resource-intensive applications with exceptional speed and performance.
Important Points to Remember:
High-end GPU variants are available for quicker processing.
Dedicated GPU servers that only your apps can use; there is no resource sharing, guaranteeing steady performance.
Parallel processing optimization enables improved output and quicker work completion.
2. Compatibility with Windows OS
For companies that depend on Windows apps, Cloudminister's GPU hosting servers are a great option because they completely support Windows-based environments.
The Benefits of Windows Hosting with Cloudminister
Smooth Integration: Utilize programs developed using Microsoft technologies, like PowerShell, Microsoft SQL Server, and ASP.NET, without encountering compatibility problems.
Developer-Friendly: Enables developers to work in a familiar setting by supporting well-known development tools including Visual Studio,.NET Core, and DirectX.
Licensing Management: To ensure compliance and save time, Cloudminister handles Windows licensing.
3. The ability to scale
Scalability is a feature of Cloudminister Technologies' technology that lets companies expand without worrying about hardware constraints.
Features of Scalability:
Flexible Resource Allocation: Adjust your storage, RAM, and GPU power according to task demands.
On-Demand Scaling: Only pay for what you use; scale back when not in use and increase resources during periods of high usage.
Custom Solutions: Custom GPU configurations and enterprise-level customization according to particular business requirements.
4. Robust Security:-
Cloudminister Technologies places a high premium on security. Multiple layers of protection are incorporated into their GPU hosting solutions to guarantee the safety and security of your data.
Among the security features are:
DDoS Protection: Prevents Distributed Denial of Service (DDoS) assaults that might impair the functionality of your server.
Frequent Backups: Automatic backups to ensure speedy data recovery in the event of an emergency.
Secure data transfer:- across networks is made possible via end-to-end encryption, or encrypted connections.
Advanced firewalls: Guard against malware attacks and illegal access.
5. 24/7 Technical Assistance:-
Cloudminister Technologies provides round-the-clock technical assistance to guarantee prompt and effective resolution of any problems. For help with server maintenance, configuration, and troubleshooting, their knowledgeable staff is always on hand.
Support Services:
Live Monitoring: Ongoing observation to proactively identify and address problems.
Dedicated Account Managers: Tailored assistance for business customers with particular technical needs.
Managed Services: Cloudminister provides fully managed hosting services, including upkeep and upgrades, for customers who require a hands-off option.
Advantages of Cloudminister Technologies Windows-Based GPU Hosting
There are numerous commercial benefits to using Cloudminister to host GPU servers on Windows.
User-Friendly Interface:- The Windows GUI lowers the learning curve for IT staff by making server management simple.
Broad Compatibility:- Complete support for Windows-specific frameworks and apps, including Microsoft Azure SDK, DirectX, and the.NET Framework.
Optimized Performance:- By ensuring that the GPU hardware operates at its best, Windows-based drivers and upgrades reduce downtime.
Use Cases at Cloudminister Technologies for GPU Hosting
Cloudminister's GPU hosting servers are made to specifically cater to the demands of different sectors.
Machine learning and artificial intelligence:- With the aid of powerful GPU servers, machine learning models can be developed and trained more quickly. Perfect for PyTorch, Keras, TensorFlow, and other deep learning frameworks.
Media and Entertainment:- GPU servers provide the processing capacity required for VFX creation, 3D modeling, animation, and video rendering. These servers support programs like Blender, Autodesk Maya, and Adobe After Effects.
Big Data Analytics:- Use tools like Apache Hadoop and Apache Spark to process enormous amounts of data and gain real-time insights.
Development of Games:- Using strong GPUs that enable 3D rendering, simulations, and game engine integration with programs like Unreal Engine and Unity, create and test games.
Flexible Pricing and Plans
Cloudminister Technologies provides adjustable pricing structures to suit companies of all sizes:
Pay-as-you-go: This approach helps organizations efficiently manage expenditures by only charging for the resources you utilize.
Custom Packages: Hosting packages designed specifically for businesses with certain needs in terms of GPU, RAM, and storage.
Free Trials: Before making a long-term commitment, test the service risk-free.
Reliable Support and Services
To guarantee optimum server performance, Cloudminister Technologies provides a comprehensive range of support services:
24/7 Monitoring:- Proactive server monitoring to reduce downtime and maximize uptime.
Automated Backups:- To avoid data loss, create regular backups with simple restoration choices.
Managed Services:- Professional hosting environment management for companies in need of a full-service outsourced solution.
In conclusion
Cloudminister Technologies' GPU hosting servers are the ideal choice if your company relies on high-performance computing for AI, large data, rendering, or simulation. The scalability, security, and speed required to manage even the most resource-intensive workloads are offered by their Windows-compatible GPU servers.
Cloudminister Technologies is the best partner for companies looking for dependable GPU hosting solutions because of its flexible pricing, strong support, and state-of-the-art technology.
To find out how Cloudminister Technologies' GPU hosting services may improve your company's operations, get in contact with them right now.
VISIT:- www.cloudminister.com
0 notes
Text
DeepSeek-R1-distilled 4bit量子化版をOllamaでGPU未使用の低スペックPCで動作させるための環境構築手順
前提条件 以下に、DeepSeek-R1の蒸留モデルをOllamaでGPU未使用の低スペックPCで動作させる手順を詳細に解説します。実際に検証済みの手順に基づいています。 OS: Windows 10/11 64bit または Linux(Ubuntu 22.04推奨) 最小要件: RAM: 4GB(8GB推奨) ストレージ: 2GBの空き容量 CPU: Intel Core i5(第4世代以降) / AMD Ryzen 3(第3世代以降) Ollamaのインストール # Windows(PowerShell) winget install ollama.ollama # Linux curl -fsSL <https://ollama.com/install.sh> | sh モデル準備(GGUF形式を使用) 公式リポジトリから量子化済みモデルをダウンロード: #…
0 notes
Text
Skills Necessary to Become a DevOps Engineer
Embarking on a career in DevOps requires a unique combination of technical and soft skills.
For those keen to excel in Devops, enrolling in Devops Course in Chennai can be highly advantageous. Such a program provides a unique opportunity to acquire comprehensive knowledge and practical skills crucial for mastering Devops.

Here’s a detailed look at the key skills essential for success in this dynamic field.
1. DevOps Principles and Practices
Cultural Awareness: Understanding the core principles of DevOps, including collaboration, automation, and continuous improvement.
2. Programming Languages
Coding Proficiency: Familiarity with programming languages such as Python, Ruby, or Java, which are crucial for automating tasks and developing software.
3. Scripting Knowledge
Shell Scripting: Skills in scripting languages like Bash or PowerShell to automate system tasks and manage environments efficiently.
4. Version Control Systems
Git Expertise: Proficiency in using Git for version control to track changes in code and collaborate effectively with team members.
5. Containerization Technologies
Docker and Kubernetes: Understanding how to use containerization tools for deploying, scaling, and managing applications in a cloud environment.
6. Cloud Computing Skills
Cloud Platform Familiarity: Knowledge of cloud services and architectures, particularly with providers like AWS, Azure, and Google Cloud, to deploy applications and manage resources.

Enrolling in Devops Online Course can enable individuals to unlock DevOps full potential and develop a deeper understanding of its complexities.
7. Infrastructure as Code (IaC)
Automation Tools: Experience with IaC tools like Terraform or Ansible to automate the provisioning and management of infrastructure.
8. Monitoring and Analytics
Monitoring Tools: Proficiency in using monitoring platforms (like Prometheus or Grafana) to track application performance and manage incidents.
9. Networking Fundamentals
Networking Concepts: Understanding basic networking principles, protocols, and security practices to maintain secure and efficient systems.
10. Soft Skills and Collaboration
Team Communication: Strong interpersonal skills to foster collaboration between development and operations teams, ensuring effective communication and shared objectives.
Conclusion
Building a successful career in DevOps demands a well-rounded skill set that encompasses both technical expertise and soft skills. By developing these key skills, individuals can effectively contribute to the seamless integration of development and operations, driving innovation and efficiency in software delivery. Continuous learning and adapting to new tools will further enhance career prospects in this ever-evolving field.
0 notes
Text
youtube
Summary
🖥️ Introduction to Macro Threats: The presentation focuses on malicious Office macros, their prevalence in attacks, and strategies to detect and mitigate them.
🛠️ Key Techniques Explored:
Baseline macro behaviors to differentiate malicious from benign activities.
Use telemetry like process trees, registry edits, and network connections to identify anomalies.
Apply tools such as Sysmon for capturing detailed process events and PowerShell scripts for advanced visualization.
🔒 Core Concepts Discussed:
Macros often exploit Microsoft Office's functionality to execute malicious payloads.
Factors like unencrypted settings and poor macro visibility increase vulnerabilities.
Hunting techniques involve comparing baseline behavior to deviations such as abnormal DLL loading or unauthorized registry changes.
📊 Key Challenges: Misaligned telemetry and lack of proper alerting strategies are barriers to effective macro detection.
Insights Based on Numbers
📈 Threat Actors: Nearly half of tracked groups use techniques involving malicious macros (e.g., T1024.002).
🔍 Visibility and Detection: Tools like Sysmon provide crucial telemetry, such as process creation, to identify anomalies effectively.
0 notes